403 forbidden page template optimized for Red Hat Enterprise Linux
Explore Similar TemplatesAbout template
Customize your Red Hat Enterprise Linux-optimized 403 forbidden page template for a flawless user experience. Get started now!
Recommended templates
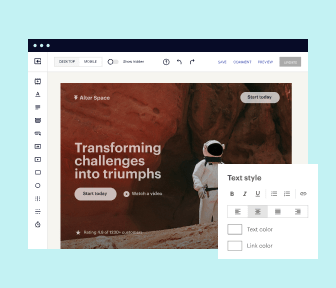
Easy to build without coding
With the intuitive drag-and-drop builder, anyone on your team can create high-converting pages without any knowledge of code or design. Make enhancements to your landing page with custom widgets using Javascript, HTML/CSS, or third-party scripts.
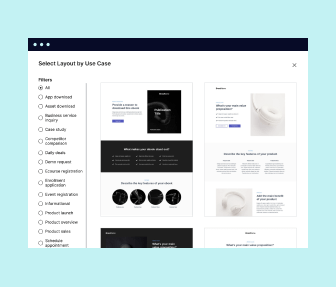
Multiple layouts for any industry and goal
Select from 500+ landing page layouts built to boost conversions across industry-specific scenarios. Customize them by adjusting fonts, adding images, and generating on-brand content with the AI assistant. Quickly scale with Instablocks® and Global Blocks that you can save, reuse, and update globally.
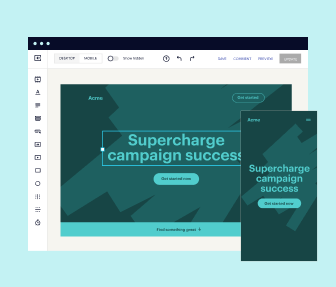
Loads fast and looks polished on any device
Every template is responsive, which means they present professionally on any device and load blazingly fast with our Thor Render Engine. You can also power them up with Google AMP technology to deliver an unparalleled mobile experience and drive higher conversions.
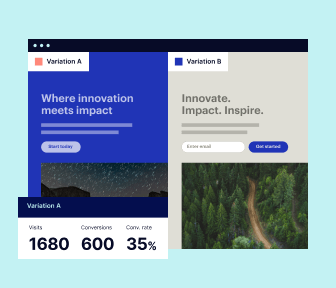
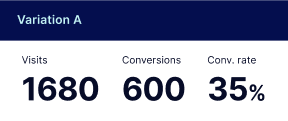
Robust analytics & experimentation
Get real-time updates and reporting across all your devices, showing the number of visitors, conversions, cost-per-visitor, and cost-per-lead. Launch AI-powered experiments, run A/B tests, and use heatmaps to analyze user behavior, then optimize your landing page to maximize conversions.

Easy to build without coding
With the intuitive drag-and-drop builder, anyone on your team can create high-converting pages without any knowledge of code or design. Make enhancements to your landing page with custom widgets using Javascript, HTML/CSS, or third-party scripts.
Multiple layouts for any industry and goal
Select from 500+ landing page layouts built to boost conversions across industry-specific scenarios. Customize them by adjusting fonts, adding images, and generating on-brand content with the AI assistant. Quickly scale with Instablocks® and Global Blocks that you can save, reuse, and update globally.
Loads fast and looks polished on any device
Every template is responsive, which means they present professionally on any device and load blazingly fast with our Thor Render Engine.
Robust analytics & experimentation
Get real-time updates and reporting across all your devices, showing the number of visitors, conversions, cost-per-visitor, and cost-per-lead. Launch AI-powered experiments, run A/B tests, and use heatmaps to analyze user behavior, then optimize your landing page to maximize conversions.
All the features you need to build lead-generating landing pages
Explore more featuresLearn how to build top-performing landing pages for any goal
FAQs
Leading the way in building high-performing landing pages





A comprehensive guide to using Instapage for landing page optimization in digital marketing
Instapage is a leading landing page and CRO platform designed to power your digital marketing campaigns efficiently. With its robust features, marketers can quickly develop high-converting landing pages, optimizing their campaigns for maximum return on investment. This guide will delve into how to leverage Instapage for effective landing pages that cater to busy marketers across various industries.
Understanding the importance of landing pages
Landing pages serve as a critical element in the digital marketing landscape. They are specifically designed to drive conversions by encouraging visitors to take a particular action. Here’s why using Instapage can enhance your marketing strategy:
- Streamlined lead generation: Instapage provides over 100 customizable templates that can be tailored to suit various campaign needs, reducing the time it takes to launch new marketing initiatives.
- Enhanced conversion optimization: With built-in experimentation features like A/B testing, you can continuously refine your pages to achieve better performance and higher conversion rates.
- Targeted personalization: Instapage allows marketers to create content tailored to specific audience segments, using features such as dynamic text replacement and audience data tracking.
Getting started with Instapage
To make the most out of Instapage, follow these key steps:
- Select a template: Choose from an extensive library of high-converting templates designed to cater to various industries.
- Customize your page: Use intuitive drag-and-drop editors to adjust your pages easily, adding elements like forms and images.
- Set up tracking: Integrate your Instapage with analytics tools to monitor page performance and user engagement.
Optimization strategies for higher conversions
Optimization is crucial to increasing landing page effectiveness. Implement these strategies for success:
- Utilize heatmaps: Analyze visitor behavior using heatmaps to gain insights on where users are clicking and what content attracts their attention.
- Conduct A/B tests: Regularly test variations of your landing pages to see which elements perform better and adjust accordingly.
- Monitor analytics closely: Use the Instapage analytics dashboard to evaluate conversion rates and user behavior metrics.
By applying these strategies, you can ensure your landing pages are consistently optimized for performance.
In conclusion, leveraging the powerful features of Instapage can significantly improve the effectiveness of your marketing campaigns. With a strong emphasis on optimization and personalization, you can achieve enhanced results and maximize ROI.
Ready to transform your marketing strategy? Sign up for Instapage today and unlock the potential of optimized landing pages!
People also ask about 403 forbidden page template optimized for Red Hat Enterprise Linux
403 Forbidden Page Template Optimized for Red Hat Enterprise Linux
Understanding the 403 forbidden error
The 403 Forbidden error is a common HTTP status code that indicates that the server understands the request but refuses to authorize it. This type of error plays a significant role in how websites manage access to resources, essentially blocking users from viewing specific pages or content. If users constantly encounter this error while trying to access certain sections of your website, it could ultimately lead to increased bounce rates and lost engagement opportunities.
The implications of a 403 Forbidden error are far-reaching, often leaving users frustrated and unsure of how to proceed. The users may question the website's credibility or reliability if they frequently encounter access restrictions. Common root causes for this error include insufficient permissions for requesting resources, incorrect configurations in the server settings, or the enforcement of credentials that have not been met.
Importance of custom 403 forbidden pages
Creating custom 403 Forbidden pages is essential for enhancing user experience during error occurrences. A well-crafted error page can significantly reduce user frustration. Instead of providing a standard error message, a custom page reinforces your brand and helps guide users toward the desired next steps. This approach encourages users to stay on the site and seek alternative content rather than leaving in dismay.
From an SEO perspective, effective handling of 403 errors can positively impact a website's crawlability and domain authority. Search engines consider user experience in their rankings, and a well-designed error page can help maintain valuable indexing. By utilizing error pages creatively, you can lead misdirected traffic to high-value content, potentially improving the site's overall SEO performance.
Optimizing the 403 forbidden page template on red hat enterprise linux
When optimizing the 403 Forbidden page template on Red Hat Enterprise Linux, server configuration is a pivotal factor. The configuration files, specifically the 'httpd.conf' and '.htaccess' files in your Apache web server, control how requests are handled and what users see when they encounter a 403 error. Properly modifying these files ensures that your customized error page is served whenever users are denied access.
Locate the 'httpd.conf' file, typically found in '/etc/httpd/conf/httpd.conf'.
Open the file in a text editor with root privileges.
Add or modify lines to specify your custom error document.
Similarly, examine the '.htaccess' file for directory-level configurations.
Ensure that the error document directive points to your custom 403 page.
Harnessing samba for file sharing
Samba facilitates seamless file sharing between different operating systems by implementing the SMB/CIFS protocol. This integration proves particularly beneficial when combined with your web server setup on Red Hat. By configuring Samba services, you can enhance resource access for users or applications that require access to specific directories or files, ultimately improving how your 403 Forbidden errors are handled.
Install Samba using the package manager with 'yum install samba'.
Configure Samba settings in '/etc/samba/smb.conf' to define shared resources.
Set appropriate permissions that correspond with your web server access controls.
Restart the Samba service to apply changes.
Test connections to ensure proper configuration.
Network and service configuration
Understanding the importance of network configuration and service access control is crucial in managing how users connect to your server and its resources. Every server runs communication via ports, which need to be properly defined to allow or restrict access. For standard web interactions, you'll often work with ports 80 for HTTP and 443 for HTTPS.
To effectively manage these ports, you must configure firewall settings in Red Hat. This involves adding rules that permit or deny traffic based on the specified access. Use tools like 'firewalld' to manage zones and make sure only the necessary ports are open to the public. By ensuring that your firewall settings align with your desired access controls, you can help mitigate potential security risks.
Verify which services require port access using 'netstat -tuln'.
Add necessary port rules using 'firewall-cmd --add-port=80/tcp --permanent'.
Reload the firewall settings with 'firewall-cmd --reload'.
Test port accessibility with tools like 'curl' or 'telnet'.
Managing domain and environment settings
Proper domain management in a Red Hat environment involves ensuring that DNS settings are accurately configured. Effective domain resolution is crucial for users to reach specific parts of your web application. Misconfigured DNS can lead to additional 403 Forbidden errors if users are wrongly redirected. Furthermore, configuring virtual hosts allows you to assign different error pages based on the requested domain or subdomain.
When setting up virtual hosts in Apache, you need to create separate configuration files for each domain or subdomain you serve. Within these configurations, you can specify custom error documents designed for the 403 error code. This structured setup will ensure users receive appropriate messages based on what they access, which in turn enhances the overall experience.
Edit or create a new configuration file in '/etc/httpd/conf.d/' for your virtual host.
Define the ServerName and DocumentRoot for each domain.
Specify the custom error document directive for the 403 status.
Check for syntactical errors using 'apachectl configtest'.
Restart Apache to apply changes using 'systemctl restart httpd'.
Authentication mechanisms for secure access
Establishing secure access through robust authentication mechanisms is necessary for web applications that store sensitive data or offer limited resources. Various methods such as Basic or Digest authentication can be implemented within your Apache configuration. These methods require users to provide valid credentials before accessing restricted content, thereby minimizing exposure to unauthorized users.
To fine-tune server authentication settings, you can utilize directives like 'Require valid-user' within your Apache configuration files. Ensure that you configure your access control rules correctly, detailing which users or user groups can access specific resources. This tailored approach to security helps protect your applications while still making it intuitive for legitimate users.
Create a password file using 'htpasswd' for Basic authentication.
Modify your '.htaccess' or your site's main configuration file to include 'AuthType Basic'.
Specify the 'AuthUserFile' and 'Require valid-user' directives.
Test access control by attempting to access protected resources.
Crafting the 403 forbidden page
When designing your custom 403 Forbidden page, it's important to include a carefully curated message that clearly explains the error's nature without overwhelming the user with complex technical jargon. Strive for concise language that informs users they do not have permission to access the requested resource. Providing an explanation helps build trust with your audience, as it keeps them in the loop about what occurred.
Apart from the error message, include links to alternative features or services. Consider directing users to popular pages or your homepage, enhancing the chances that they will find something else of value rather than leaving your site altogether. Encouraging exploration even when encountering an error can lead to conversion opportunities.
Use a clear title like 'Access Denied' or '403 Forbidden'.
Include a brief explanation of the error.
Offer links to your homepage or a support page.
Maintain a consistent layout that reflects your brand.
Consider adding a search feature for easy navigation.
Utilizing posix acls to manage access control
POSIX ACLs (Access Control Lists) provide a granular way to manage file permissions on a Red Hat system. Unlike traditional UNIX permissions, which only allow for owner/group/other classifications, ACLs give you the flexibility to define permissions for specific users and groups. Utilizing POSIX ACLs can help you tailor access to resources that are behind 403 errors, ensuring only authorized users can access sensitive content.
Implementing POSIX ACLs begins with verifying that the ACL capability is enabled on your filesystem. You can then apply changes using commands like 'setfacl' to define specific user permissions. This tailored approach to access management minimizes the chances of unauthorized access while allowing legitimate users to interact with the system fluidly.
Check if ACL is enabled with 'mount | grep acl'.
Use 'setfacl -m u:username:rwx /path/to/resource' to set permissions.
Verify permissions with 'getfacl /path/to/resource'.
Adjust as necessary to ensure proper access rights.
Verification and testing procedures
Verifying your server configuration for proper handling of 403 Forbidden errors involves several essential commands. You can utilize 'curl' to send requests to your server and examine the resulting HTTP status codes. Another useful tool is 'telnet,' which allows you to test TCP connections to the configured ports. These methods provide quick insight into whether users can access the designated resources.
In addition to connectivity tests, validating the proper functioning of your 403 error pages is crucial. You can access resources that should trigger a 403 error to ensure that your custom error message appears as expected. If your custom error page doesn't render correctly, you may need to revisit your configurations to identify and rectify any errors.
Use 'curl -I ' to check the status code.
Test specific ports with 'telnet yourwebsite.com 80'.
Access URLs known to trigger 403 to verify custom error pages.
Review server error logs for further insights.
Monitoring and logging for enhanced performance
Monitoring server performance and having robust logging mechanisms in place are paramount for effective troubleshooting of 403 Forbidden errors. Apache server logs, situated typically in '/var/log/httpd/', maintain records of all access and error events. Regularly reviewing these logs can provide crucial insights into what's happening when users encounter problems.
By configuring error logging appropriately, you can pinpoint the origins of 403 errors with greater clarity. Aligning these logs with your monitoring practices allows you to identify patterns in user behavior or access issues. Therefore, enabling detailed logging settings equips you with the necessary tools to address and mitigate any access-related challenges efficiently.
Check Apache log configurations in 'httpd.conf' or respective vhost files.
Monitor access logs using 'tail -f /var/log/httpd/access_log'.
Review error logs similarly with 'tail -f /var/log/httpd/error_log'.
Generate periodic reports based on log analysis.
Advanced techniques for 403 page optimization
To boost user retention even when faced with a 403 error, consider implementing dynamic content delivery for your error page. By integrating database solutions to fetch real-time updates, you can personalize the user experience tailoring the content based on user interaction history or preferences. Such improvements can help create a more engaging alternative for users who might otherwise leave your site.
Using frameworks and middleware in your application architecture can also enhance functionality. Popular options within a Red Hat environment can simplify how custom pages behave and engage. Frameworks like Django or Flask provide robust mechanisms to handle such exceptions and customize responses effectively, maintaining consistency across your web application.
Explore middleware options for enhanced application control.
Integrate a database to provide real-time updates on your 403 page.
Utilize frameworks for streamlined customization and handling.
Continuously adapt to the behavior of users interacting with the error pages.
Best practices for maintaining your custom 403 page
Routine configuration audits ensure that your server remains optimal and does not harbor any vulnerabilities that could affect user experience. Regular audits can help identify configuration anomalies or task completion failures that may inadvertently lead to increased occurrences of 403 errors. By conducting a thorough review of your settings regularly, you can implement necessary updates or adjustments proactively.
Furthermore, future-proofing your web application's configuration is essential. As network services and database frameworks undergo continual advancements, maintaining your server’s compatibility with these technologies is vital. Stay updated on industry trends and security vulnerabilities while also gently evolving your error handling strategies and custom pages.
Schedule regular audits to review configurations.
Document changes meticulously for future reference.
Stay informed about new security threats and patches.
Adapt quickly to new technologies relevant to your server.
Conclusion: The impact of effective 403 forbidden page management
In summary, adopting a customized error handling strategy for managing 403 Forbidden pages on Red Hat Enterprise Linux significantly impacts both user experience and overall site performance. Custom pages crafted with intention can transform a frustrating situation into a meaningful interaction, encouraging continued engagement with the website. The approach to server configuration, network management, and continuous optimization ultimately leads to a robust user experience.
As such, investing time and resources into optimizing your 403 Forbidden page is necessary as it plays a crucial role in enhancing user experience and preserving brand integrity. By adopting a holistic approach to server management, websites can provide a seamless experience to their users, enhancing trust and loyalty, ultimately contributing to higher conversion rates and improved overall performance.
Ready to skyrocket conversions?
Supercharge your ad campaigns with high-performing landing pages
Get started